Understanding and Mitigating Distributed Denial of Service (DDoS) Attacks
In the vast landscape of Africa’s digital frontier, a menacing force lurks in the shadows, seeking to disrupt the normal operations of our digital entities. This force,...
20/09/2023 | 2 Minute Read
Principal Software Engineer

In the vast landscape of Africa’s digital frontier, a menacing force lurks in the shadows, seeking to disrupt the normal operations of our digital entities. This force, known as a Distributed Denial of Service (DDoS) attack, operates on a principle distinct from many other cybersecurity threats. Instead of stealthily infiltrating systems, DDoS attacks aim to render their targets completely inaccessible.
In this article, we embark on a exploration of DDoS attacks, delving into their fundamental nature, intricate mechanisms, and proactive mitigation strategies. We aim to equip readers with a profound understanding of these threats, their origins, and the measures available to safeguard against their disruptive capabilities.
Defining the DDoS Menace: What is a Denial of Service (DDoS) Attack?
At its core, a Distributed Denial of Service (DDoS) attack is an endeavour to disrupt the normal operations of a digital entity, be it a website, an online service, or an entire network. Unlike many cybersecurity threats that seek to infiltrate, compromise, or steal data, DDoS attacks operate on a different principle – they aim to render their target completely inaccessible.
Imagine, for a moment, a digital traffic jam of such colossal proportions that it paralyses the highways of data flowing across the internet. Rather than stealthily infiltrating a system, the attacker orchestrates an overwhelming flood of internet traffic, akin to a tsunami crashing upon the shores of a digital fortress.
The Anatomy of Chaos
To comprehend a DDoS attack, one must delve into its intricate anatomy. The orchestrator of a DDoS onslaught typically enlists the help of a legion of compromised computers, cloud workloads and mobile devices, collectively known as a botnet. These unwitting accomplices, often scattered across the globe, are harnessed to carry out the assault. When the signal is given, this legion springs into action, inundating the target with a deluge of data requests and traffic, far beyond what it can handle. The result is akin to trying to sip from a firehose – a flood of data that overwhelms, incapacitates, and eventually brings the targeted system to its knees.
In the following sections, we will explore the mechanics of DDoS attacks in greater detail, shedding light on their various forms and the motivations behind them. We will also discuss their impact on individuals and organisations, emphasising the critical importance of understanding and mitigating this ever-present digital menace.
Uncovering the Driving Forces: What Motivates DDoS Attacks?
Understanding the motivations behind Distributed Denial of Service (DDoS) attacks is crucial to comprehending the full spectrum of this digital threat. DDoS attacks are not a one-size-fits-all menace; they can be driven by a range of motives, each with its own set of objectives.
Competitive Advantage
Organisations in the online space will have competitors offering the same services, some entities resort to DDoS attacks as a means of gaining a competitive edge. By disrupting the online services of a rival company, attackers can divert traffic to their own offerings, potentially boosting sales and market share.
Hacktivism
Hacktivists leverage DDoS attacks as a digital form of protest or activism. Their motivations may be rooted in political, social, or ethical causes. By targeting government websites, corporations, or institutions, hacktivists aim to raise awareness of their grievances or disrupt the operations of entities they oppose.
Extortion
DDoS attacks can be used as a tool for extortion. Attackers threaten to launch a devastating DDoS assault against a target unless a ransom is paid. Victims, often faced with the prospect of significant financial losses due to service downtime, may opt to pay the ransom to mitigate the attack.
Revenge
Personal vendettas and disputes can lead individuals to launch DDoS attacks against specific targets. These attacks may be motivated by a desire for revenge, retaliation, or a sense of injustice.
Distraction
In some cases, DDoS attacks are used as a diversionary tactic. While defenders are preoccupied with mitigating the DDoS assault, attackers may exploit vulnerabilities in the target’s security to carry out other, more sinister actions, such as data breaches.
Beyond Capacity: Navigating the Onslaught of a Billion Requests
Application architecture is primarily designed to serve customers, and best practices involve accommodating spikes in traffic based on trends in daily business operations. It is not practical to cater to 1 million daily visitors if your daily traffic typically ranges from 1000 to 5000 users. This would result in an expensive cloud bill for underutilised cloud resources.
DDoS attacks exploit the delicate balance between cost and availability in your infrastructure. They cripple systems by pushing them beyond their workload capacity, including web server capabilities and load balancer maximum input-output per second (IOPS) thresholds.
When considering real-world scenarios, one must ask: What happens when you suddenly receive an additional 1 billion requests without prior notice? Is your business adequately prepared?
The graph below illustrates CloudFlare’s Web Application Firewall (WAF) defending against approximately 1 billion requests during a 2-day DDoS campaign.
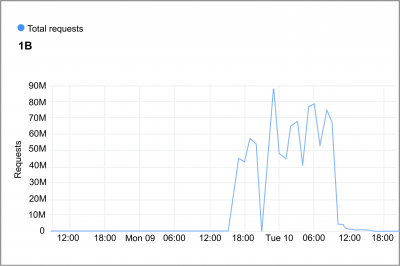
To gain a comprehensive understanding of the risks and approach a DDoS attack with the appropriate actions, one must adopt a critical approach to make swift yet effective business and technical decisions. These decisions are crucial in maintaining maximum uptime for your business.
Service Disruption
Has the attacker conducted thorough research on your system in the public domain? Are they specifically targeting weaknesses, such as an unoptimized API request or a webpage that imposes an excessive load on your web server? Understanding the DDoS attacker’s intentions can reveal whether they are focused on disrupting a particular business process or functionality of your website, with the goal of denying service or affecting your inventory.
Cost and Time to Execute the DDoS Campaign
DDoS campaigns demand time, effort, and computational resources. The disruption in service exacts a toll on a business, leading to both financial losses and reputational damage. For the attackers, there are costs, financial risks, and potential gains associated with carrying out the attack. It is essential to treat every DDoS attack seriously, considering the possibility of financial gain for the attackers.
Duration of the Campaign
Even when protected by a Web Application Firewall (WAF), it might seem like the attack is just automated traffic hitting a brick wall. However, don’t lose sight of the DDoS attack’s objective. Longer-lasting attacks provide attackers with opportunities to learn more about the landscape, allowing them to adapt their tactics, search for vulnerabilities in the infrastructure’s security, and probe the DDoS protection for weaknesses.
Attack Vectors
DDoS attacks can take different forms. They may employ brute force by flooding a service with a massive amount of traffic, aiming to cripple it. Alternatively, DDoS attacks can obscure vulnerability scans, suggesting that the attackers are creating noise in an attempt to identify and exploit system vulnerabilities by targeting multiple ports and URLs.
Communications and Social Media Presence
In many DDoS attacks, the objective is to gain notoriety. Attackers may achieve this through social media posts, online messages, or emails sent to top executives within an organisation. Paying close attention to any suspicious communications received from attackers is essential for comprehending the rationale behind the attack.
Geographical Distribution of the Attack
Understanding whether the attack originates from a distributed botnet is crucial for effective mitigation and safeguarding against unwanted traffic. Websites often operate within specific regions and territories, and their user traffic exhibits location-based trends. If the botnet’s origin does not align with expected visitor traffic, implementing measures to block bot traffic in specific regions becomes more effective.
Below is a heatmap of what a botnet attack spanning 1000s of devices across multiple countries appear as in CloudFlare’s Dashboard with indication of the top sources:
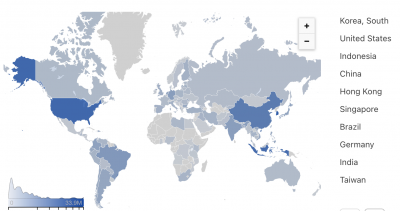
By thoroughly investigating and assessing the attack landscape, businesses can configure firewall rules and make informed decisions to mitigate the impact of the attack to the greatest extent possible.
Cat and Mouse Game: Adaptation and Attack Evolution
Mitigating DDoS attacks presents a challenging reality where attacks are in a constant state of flux. Attackers continually pivot to alternative methods and mechanisms throughout the attack duration.
Prioritising operational uptime while striving to enhance availability with minimal impact is instrumental in keeping both a website and a business operational during these assaults. It’s essential to acknowledge that achieving 100% uninterrupted service during an attack may not always be possible. There will inevitably be instances of legitimate traffic being inadvertently blocked.
The goal is to minimise these false positives by adapting to attack patterns and making real-time adjustments to firewall configurations and rules during the attack.
Every control implemented to mitigate an attack can and will be scrutinised by attackers. They will pivot their DDoS attack strategies to circumvent the security measures in place. The key lies in staying ahead of the curve by comprehending the evolving situation and being prepared to pivot security controls and WAF configurations in response to changing attack patterns.
Conclusion
As part of Deimos’ security offerings, we provide configuration, setup, and insights into CloudFlare’s Web Application Firewall functionality. Our team of engineers is well-prepared to respond and assist in mitigating DDoS attacks, ensuring that our clients can maintain operational resilience during these types of cyberattacks.
While there is no silver bullet for defending against DDoS attacks, taking proactive measures to implement necessary security controls is paramount. This proactive approach is key to safeguarding businesses in the cloud and the public internet space, protecting them against threats like DDoS attacks. By staying vigilant and well-prepared, organisations can significantly enhance their ability to withstand and counter these evolving cyber threats. To learn more on how Deimos can help you protect your business, click here.